EASM platform: Asset Discovery & Inventory
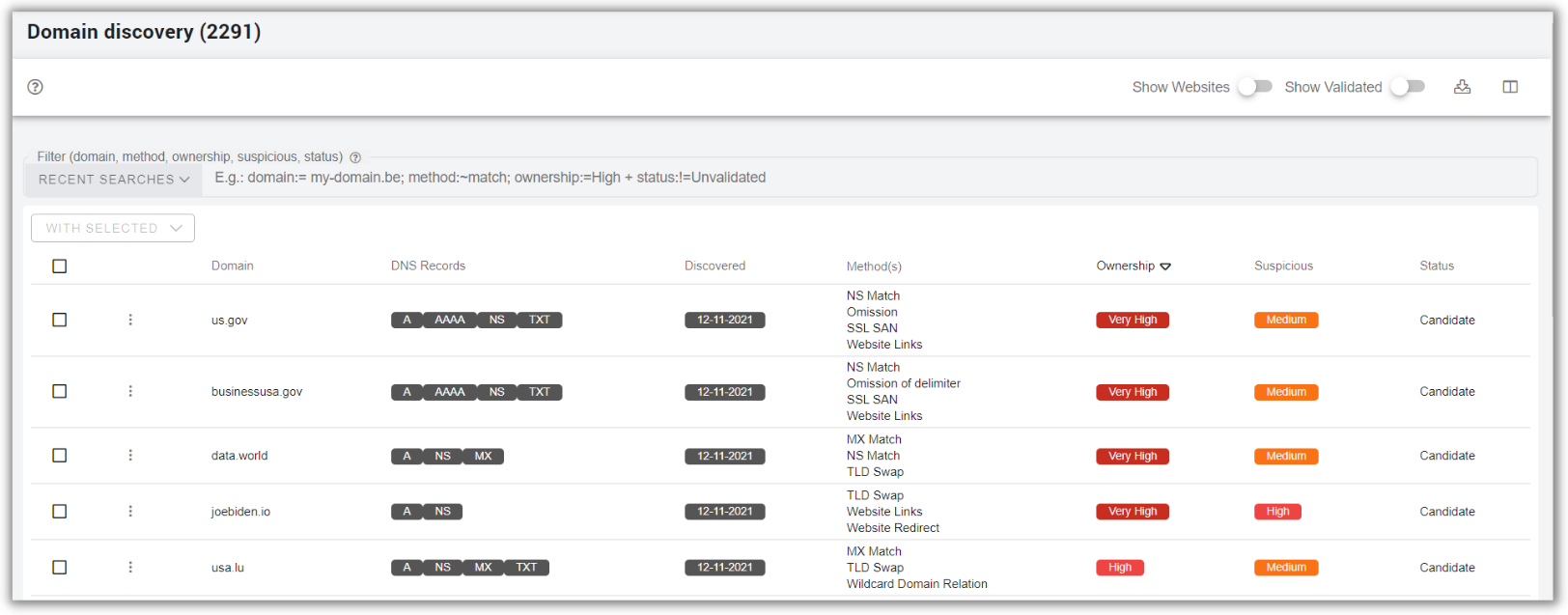
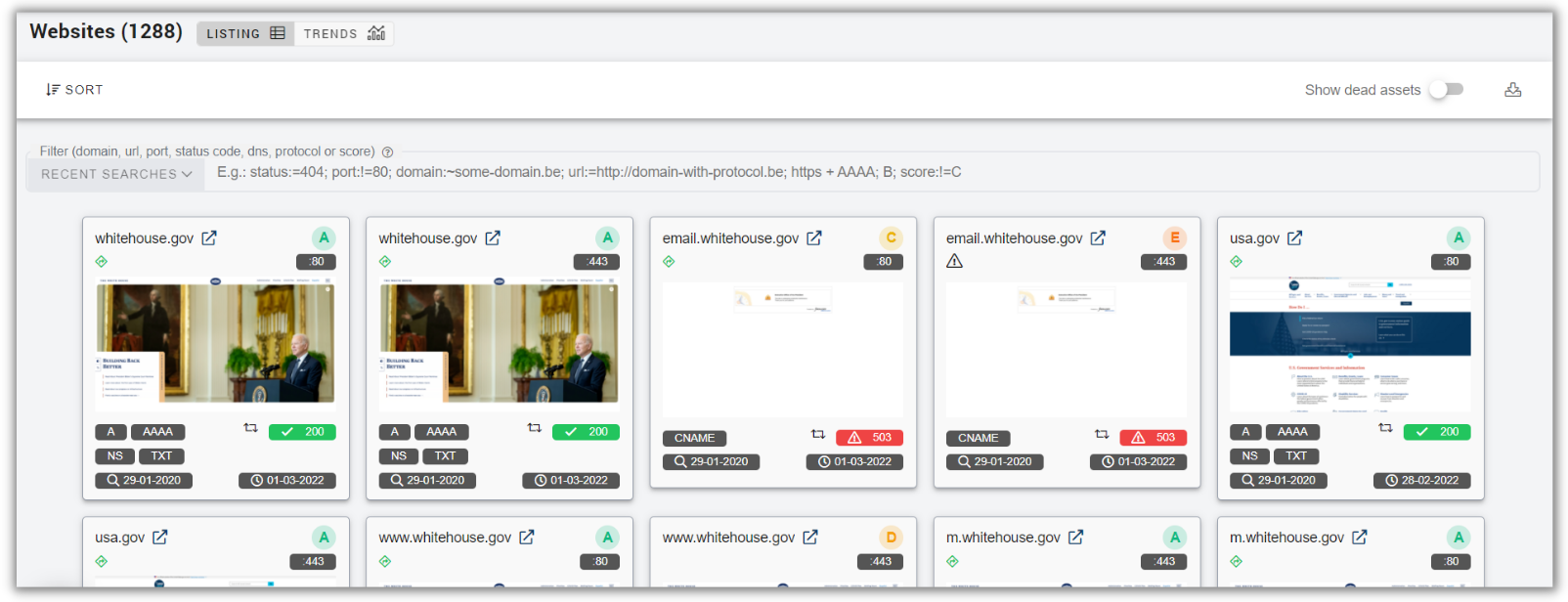
The Sweepatic Platform discovers and inventories all internet-facing assets connected to your organization. This includes unknown and unmanaged IT assets that you get visibility on and that will automatically stay up to date in the central internet-facing assets inventory.
What you know, you can protect!
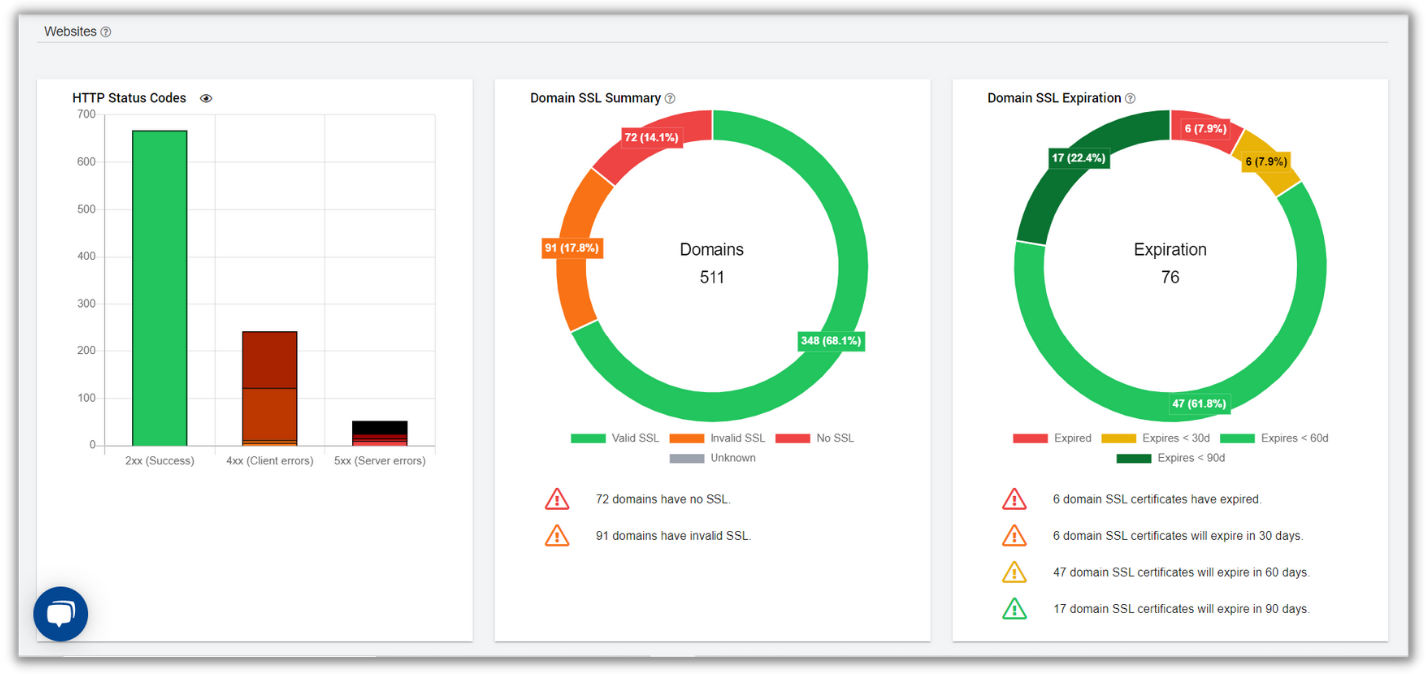
In the Platform itself, the Dashboard provides real-time status of the attack surface, including visual representations and trends.
Furthermore, notifications are sent when a new asset discovery or attack surface change occurs leading to prioritized observations you (urgently) need to take a look at.
Using our integration options e.g. e-mail, webhook, or API, you can be alerted directly in your existing tool stack.
Advanced Reconnaissance
In the first phase of the Cyber Kill Chain, bad actors perform reconnaissance on organizations to select their victims.
They will try to find everything they can on the company, including all online exposed assets. By mapping and knowing your attack surface before cybercriminals do, you can prevent cyberattacks by reducing your online exposure and removing assets without business justification, fixing misconfigurations, remediating security issues and risks and cleaning up your attack surface to make it as lean and agile as possible. And thus less attractive for cyber criminals to break into.
Continuous monitoring
An inventory of assets connected to the internet is extremely important, but it needs to stay up to date.
The Sweepatic platform automatically and continuously monitors your organisation’s discovered attack surface for changes. Be the first to know when your attack surface changes or problems, vulnerabilities or misconfigurations emerge.
Request your demo
Do you want to experience what Sweepatic can do for you?
Improve your cyber resilience and request a free, personalised demo.
We will map your current situation and provide a list of relevant, actionable insights.
You can start to take action immediately after.