Home > Request your demo
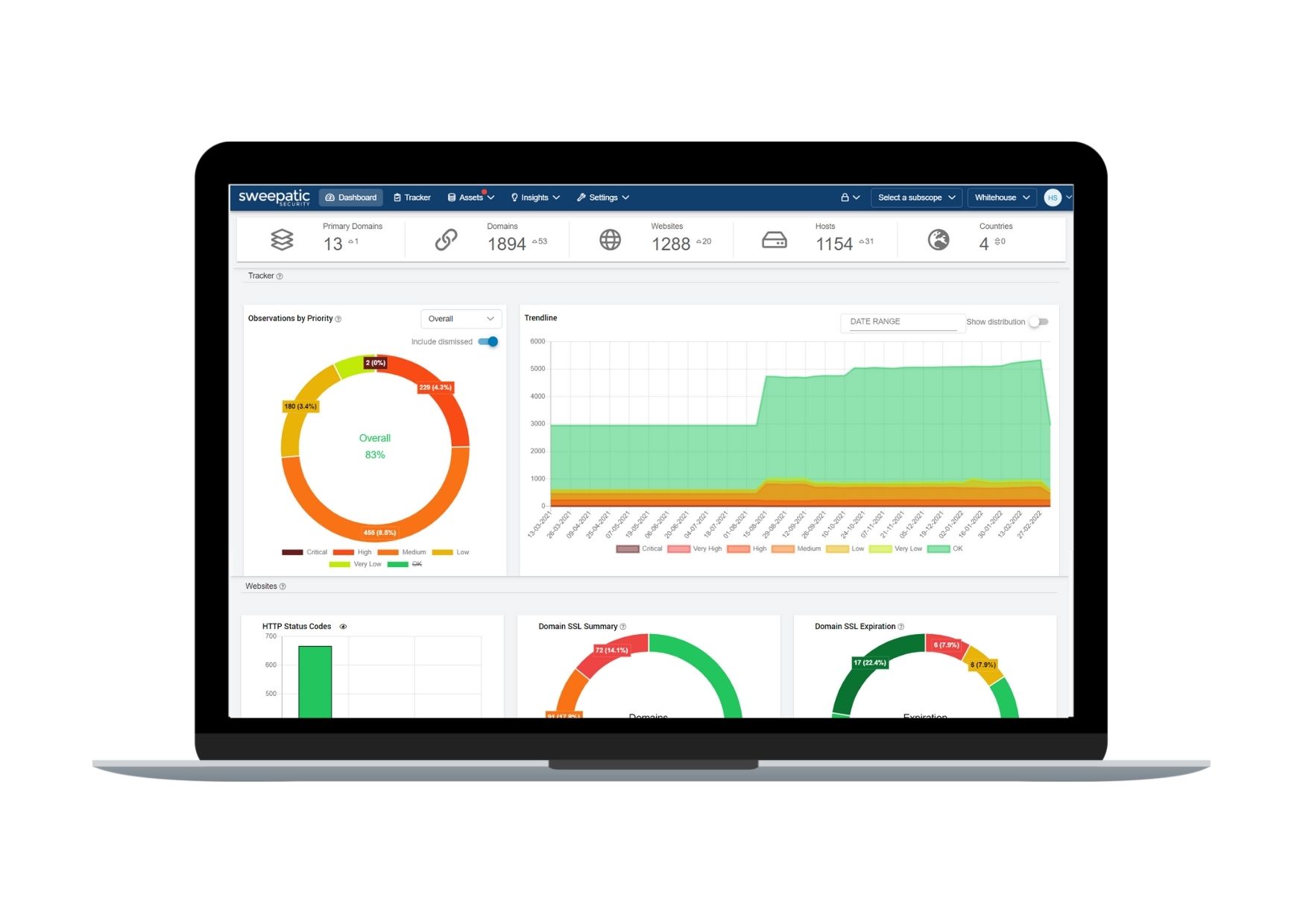
Map, analyze and monitor your external attack surface
- How can my organization become a less attractive target for cyber attacks?
- Which assets are exposed in my attack surface?
- What remediations are required to get my attack surface in order?
- What are priority actions to take?
Request your free demo
Do you want to experience what Sweepatic can do for you?
Improve your cyber resilience and request a free, personalized demo.
We will map your current situation and provide a list of relevant, actionable insights. You can start to take action immediately after.
What you obtain from the demo:
- insights to improve your posture
- your internet-connected assets
- the location of your hosts
- open ports and vulnerable assets
- a list of your cloud providers
- forgotten and unsecure web applications
- and much more …

“The issue I encountered was a lack of visibility. From a security point of view, not knowing what you have somewhere on the internet and what its status is – both from a technical and regulatory point of view – is like a blind man driving towards a big wall.”
– Peter Van Lierde, CISO at Sibelga

“Most of the time classic methodologies, like an ad hoc pentest or vulnerability scans, are just spot-checks. With Sweepatic we have continuous scanning enabled on our external attack surface and constant access to that information and data in a user-friendly interface.”
– Laurent Joppart, CISO at Nationale Loterij
European leader in External Attack Surface Management







