
Home > Sweepatic EASM introduces Threat Intelligence

TI data added to the Sweepatic EASM Platform
The first integration since the acquisition by Outpost24 is a fact: The Sweepatic External Attack Surface Management Platform now integrates Outpost24’s Threat Compass solution delivering leaked credentials found in your external attack surface. This feature – by means of a free teaser – will be gradually activated for all Sweepatic customers. Of course, a full integration will be available too.
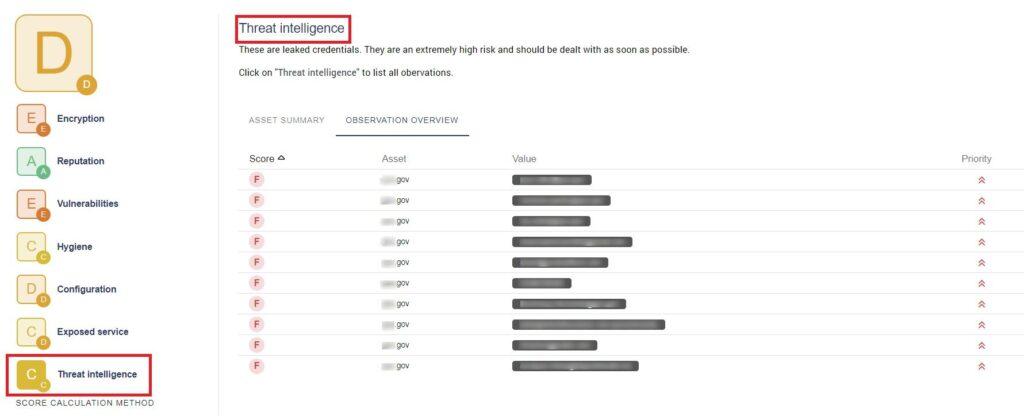
This also means a 7th cybersecurity dimension was added to the dashboard, called Threat Intelligence. You can check out your leaked and stolen credentials observations there or in the Tracker.
Why is it important?
Any organization with an online presence has sensitive data, valuable to bad actors. When financial information, personal identifiable information (PII), confidential company data, industrial IP, etc. falls into the wrong hands, it can have enormous consequences for the company, from business impact, reputational damage to fines and compliance penalties.
Therefore, it is key to stay alert to this threat and continuously monitor and follow up on targeted, actionable threat intelligence data. Automating this cybersecurity resource saves time and gives your organization a proactive advantage against attacks.
What's in it for you?
The new TI feature in the Sweepatic EASM Platform will help you find out if users of any of your domains have had their credentials leaked. Meaning, are there any passwords matched with user email addresses or user names found online? We make a distinction between leaked and stolen credentials.
Leaked credentials refer to personal information that fell into the hands of a bad actor due to human error. Stolen credentials are often the result of a breach or attack where the bad actor actively steals the sensitive data. In the Sweepatic EASM Platform you will see the discovered observations for both hacktivism (from cybercrime forums, paste sites, P2P, dark web sites, …) and botnet credentials (stolen by crime servers), as well as information on the source, timestamp, the threat actor involved (if this particular info is available).
If a leaked or stolen credential is found, the recommended action would be to alert the user to update their password, including other platforms where this username and password is used, and/or block their access.
Leaked credentials represent a high risk and have a high priority to solve!
What's next?
Keep a close watch on our announcements, as we have new TI options coming right up! Our developers work on various features to enhance insights into your external attack surface presence.
By the way, if you require some structural mitigation help, check out our managed services offering.
Request your personalized demo
Curious to see what the Sweepatic External Attack Surface Management Platform can do for your organization? Request a personalized demo!
Follow us on LinkedIn and Twitter and subscribe to our newsletter to get the scoop on company news and new blogposts!



