Threat Intelligence
Any organization with an online presence has sensitive data, valuable to bad actors. When financial information, personal identifiable information (PII), confidential company data, industrial IP, etc. falls into the wrong hands, it can have enormous consequences for the company, from business impact, reputational damage to fines and compliance penalties.
Therefore, it is key to stay alert to this threat and continuously monitor and follow up on targeted, actionable threat intelligence data. Automating this cybersecurity resource saves time and gives your organization a proactive advantage against attacks.
Track leaked and stolen credentials
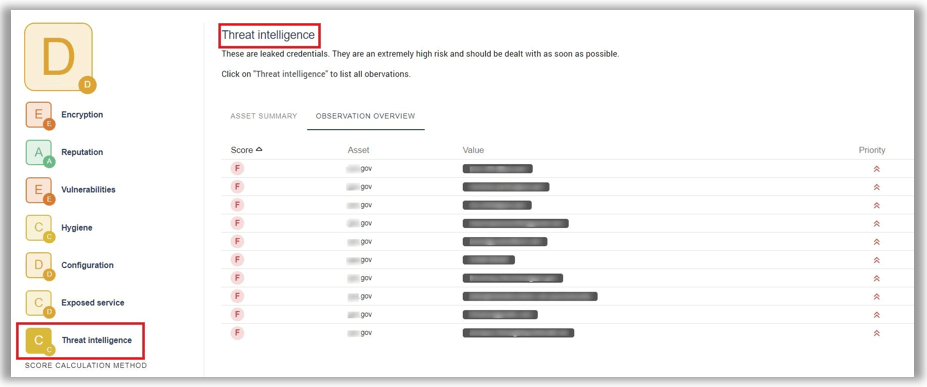
The threat intelligence feature in the Sweepatic EASM Platform will help you find out if users of any of your domains have had their credentials leaked. Meaning, are there any passwords matched with user email addresses or user names found online?
If this is the case, the recommended action is to alert the user to update their password, including other platforms where this username and password is used, and/or block their access. Leaked credentials represent a high risk and have a high priority to solve!
Resources
Read more in the blogposts below.
Request your demo
Do you want to experience what Sweepatic can do for you?
Improve your cyber resilience and request a free, personalised demo.
We will map your current situation and provide a list of relevant, actionable insights.
You can start to take action immediately after.