Home > Discover and assess rogue technologies across your attack surface
This blogpost will explain how 3rd party technologies used to build your online web presence are exposed online. Those technologies and frameworks are also an often overlooked part of your organization’s attack surface. The Sweepatic Platform discovers and tracks these technologies for you so you can monitor, analyze and take appropriate action in case they badly impact your organization’s security posture.
Knowing your organization’s infrastructure is always the first step in protecting it against threat actors. After all what you don’t know, you can’t protect!
Why is it important?
The last decade has been one of digital transformation. Organizations move to the cloud, implement automation in their daily tasks (e.g. marketing automation) and gather massive amounts of data via (analytics) tools and platforms.
According to a TechRepublic survey, nearly 70% of companies are either using or considering cloud services. On top of that, TechJury states that by the end of 2020, 67% of enterprise infrastructure will be cloud-based. In their article about digital transformation statistics, Finances Online reveal that 70% of organizations have a digital transformation strategy or are working on one, and the top five technologies already implemented include big data/analytics (58%), mobile technology (59%), and APIs and embeddable tech (40%).
Organizations rely more and more on a multitude of technologies to conduct their online business. Apart from this technology overflow, it is important to know that each 3rd party technology within your attack surface has an attack surface of its own.
Let’s take a closer look at what this means for your organization.
Digital transformation and technologies overflow
The trend of digital transformation, digital adoption, and continuous software improvement results in a technology overflow in your environment.
(...) We define digital transformation as the integration of digital technology into all areas of a business resulting in fundamental changes to how businesses operate and how they deliver value to customers.
Digital adoption is defined as achieving a state in which digital tools are being used as intended, and to the fullest extent. Digital adoption happens when technology becomes second nature to its user.
In other words: attack surfaces are continuously growing because organizations use multiple digital platforms and 3rd party technologies to conduct online business. Apart from employees making human errors when using and leveraging this multitude of software, a lack of overview can cause problems too.
It is easy to get lost: your brand’s online presence is built on content management systems (e.g. WordPress), analytics tools (e.g. Google Analytics), web frameworks (e.g. Java), server software (e.g. Apache), ecommerce tools (e.g. Shopify), captchas (e.g. reCAPTCHA) and more 3rd party technology suppliers.
Security holes and data breaches
Not only are these 3rd party technologies a part of your organization’s attack surface, these elements also have an attack surface of their own. We know that technologies contain vulnerabilities, can be discovered and hacked over time by bad actors.
Take a look at these historical incidents:
In 2018 British Airways reported they had been hacked and sensitive information from thousands of their customers had been stolen. The cause of the breach was malicious 3rd party code.
A similar attack happened to Capital One, where a hacker took advantage of a Amazon server misconfiguration.
In December, word got out that a database containing information on Honda owners in North America was exposed online. An Elasticsearch cluster containing this data was reachable via the internet without authentication.
Threat actors are known to exploit JavaScript security holes for advanced attacks, for example to steal sensitive information from website visitors.
In a nutshell: it is your company’s responsibility to monitor and manage your online attack surface and all its digital building blocks and make sure you have the visibility and control to take action if your organizational security posture and reputation is degrading.
Do you know your attack surface?
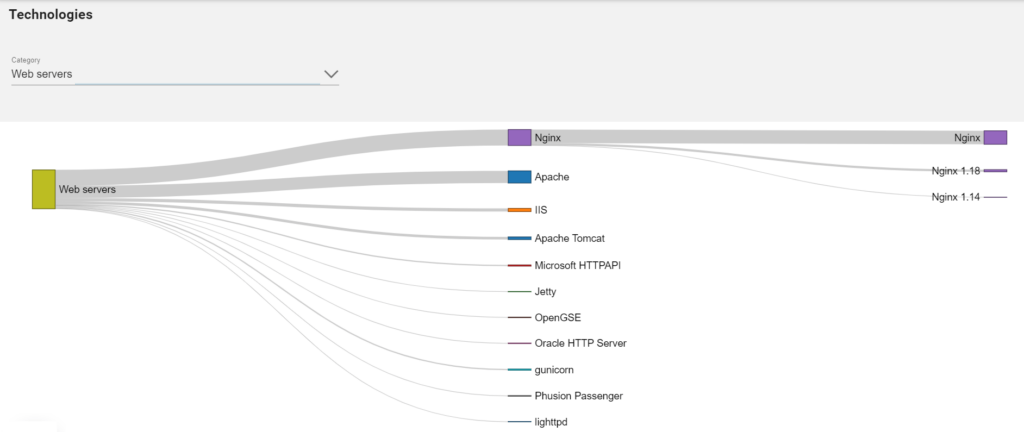
The Sweepatic Platform discovers a wide variety of technologies across your attack surface. This 3rd party framework discovery is integrated in the Sweepatic secure portal, so you can have a clear, centralized view on all your internet-facing assets and the technologies related to them.
What if, for example, a vulnerability is discovered in WordPress or Drupal? Do you know where all your WordPress and Drupal instances are residing? Do you know which version is running in your organization? You can find out with just a few clicks in the Sweepatic Platform.
If a 3rd party vulnerability is discovered, you need to know where your internet-facing assets that are related to this technology are residing to take immediate action and protect your organisation from harm.
Through the Sweepatic Platform asset tagging, actionable insights and notifications around outliers, unknown, rare and outdated technologies and version numbers are supported, across your entire internet exposed attack surface.
Contact us
We at Sweepatic are continuously engineering new use cases for our Sweepatic Platform to support our customers in running successfull attack surface management programs.
These use cases are delivered to our users in various ways, including machine readable exports, API access, a portal and/or intelligence reports.
So if we sparked your interest and you would like more information, don’t hesitate and reach out to us via info(at)sweepatic.com or ping us via our social media channels.
For a free trial of the Sweepatic Platform click here!