Home > USA.gov vulnerable to Subdomain takeover
What would you say if one day you are visiting usa.gov and you’d see this screen:
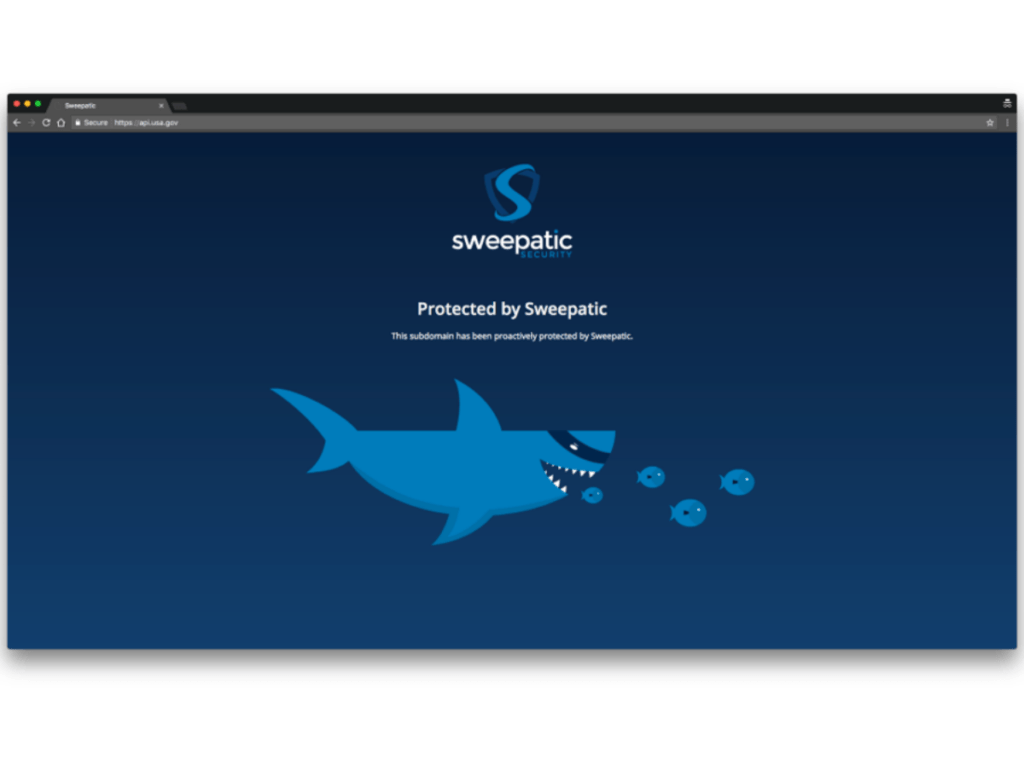
What are those fishes doing on the official USA Government Website??
Well, this actually happened! Through our reconnaissance platform we are able to do targetted queries and find suspicious domains. When checking the USA.gov domain we discovered a significant security gap which enabled us to take over their subdomain. Of course, we then secured it from hostile hackers and through coordination by the National CSIRT in the US we helped to make USA.gov aware of this significant security gap.
In this blog post we will explain and show to you what exactly happened and how you can protect your organization from those very “Subdomain Takeovers”. If you’re asking: what’s this?, here’s our blog post on the principles of a Subdomain Takeover. It covers, with great detail, how a takeover is done and of course how to take decrease vulnerability.
So what happened to usa.gov?
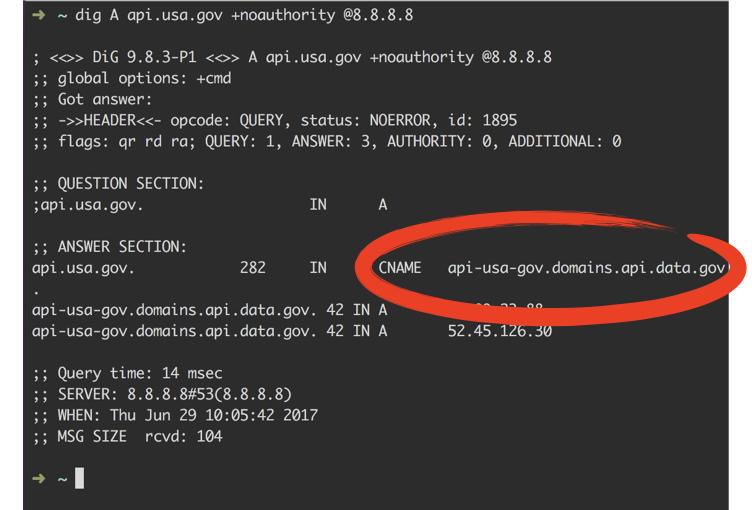
With our reconnaissance platform, we are able to search the internet for targetted queries. This enables us to spot suspicious Subdomains for any domain we are checking. In the USA.gov case, the suspicious subdomain was called api.usa.gov.
After an inspection by our expert hunters, we found it pointed to api-usa-gov.domains.api.data.gov using a CNAME DNS record.
This api-usa-gov.domains.api.data.gov has A records pointing to the GitHub infrastructure, but unfortunately the api.usa.gov subdomain is not registered in GitHub anymore. Consequently, the domain api.usa.gov can be registered by any attacker who in return will have full control over one of the USA.go subdomains.
A vulnerable domain like this presents many options to an attacker. It is a perfect infrastructure for
- Phishing
- Malware spreading
- Cookie extraction
- “Man-in-the-browser” attacks
- USA.gov brand damage
This makes it clear: a subdomain takeover represents and is considered a high risk.
How to protect/repair the domain?
In order to protect the domain, remove the CNAME record of this subdomain or point it elsewhere.
As already mentioned above, our blog post on the principles of a Subdomain Takeover will explain all of this in more detail.
Responsible disclosure
After having secured the domain, we contacted the National CSIRT in the US, who coordinated the responsible disclosure to USA.gov. We believe this is a prime example collaboration between the private and public sector and governmental bodies. In the future, this collaboration will be crucial in order to ensure the best possible security in cyber space.
This was also confirmed at the 5th European Annual Cyber Security Conference in Brussels this year, as this exact collaboration was one of the major talking points in the agenda.