
Home > Mapping your attack surface

Digital dependence under control
Digital dependence is a part of many businesses’ functions. Applications, solutions, data — everything is online. And since the number of all technologies used by companies among various departments is rapidly growing day by day, so is the attack surface. Therefore, awareness of your organization’s online surface is key in our digital-dependent reality. With External Attack Surface Management, you can map, monitor, and analyze all external security issues, like leaked credentials, misconfigurations in email/DNS/Web, expired or weak SSL certificates, exposed databases, weak encryption, GDPR compliance, and much more.
Attack surface mapping – scope definition
One of the deliverables of EASM is to provide insights into unknowns. In this sense, we can say that the EASM Platform works like a live attack surface mapping tool. And all its findings are collected under the scope — the range of the external attack surface of the company. Consequently, all vulnerabilities found within, including the forgotten, unknown, or unattended domains, technologies, websites, etc. are gathered in one place for further analysis.
EASM uses a zero-knowledge approach. This means the Platform starts mapping and scanning external IT assets with limited data, for example, a company name or primary domain information. The onboarding process is super quick and easy.
Nevertheless, it’s crucial to maintain a thorough and precise scope definition to always stay a step ahead of bad actors. This proactive approach guarantees that the Platform is continuously providing accurate and relevant information for effective risk management.
The good news is that you don’t have to spend much time adjusting your scope at any time. EASM Platform has a powerful automatic Domain Discovery module looking for everything you own (or possibly own) online.
Below, you can find a summary of all the options you can choose from that keep your scope up to date.
Manual setup
- Add primary domains
This is a default option. As soon as the EASM Platform receives information about at least one of your primary domains, it enables the search engine to map and inspect the company’s digital surface.
Alternatively, it is also possible to:
- Add IPs/IP ranges
The use of this feature isn’t mandatory. It may be helpful, for example, if you would like to scan only specific IP ranges associated with a particular project.
- Add subdomains
Specifying subdomains isn’t necessary since they will be automatically discovered. Manual addition is available should specific subdomains be missing in the scope.
- Add a cloud integration
You can add an integration with Amazon Web Services (AWS) and/or Microsoft Azure to regularly retrieve Route 53 and DNS Zone data. Thanks to that, you can boost findings and keep track of your domains.
Automatic scope discovery
Unknown online company presence is detected thanks to the following automatic features:
- Domain Discovery
Our Domain Discovery module is designed to find everything you own online. This module detects primary domain candidates and delivers a verified list of look-a-like domains with an “Ownership” and “Suspicious” qualification level. What’s more, you can see a screenshot of the domain, and of course, there are a couple of options, to decide what to do with this discovery (dismiss, monitor, add to your primary domains, or add to a potential primary domains).
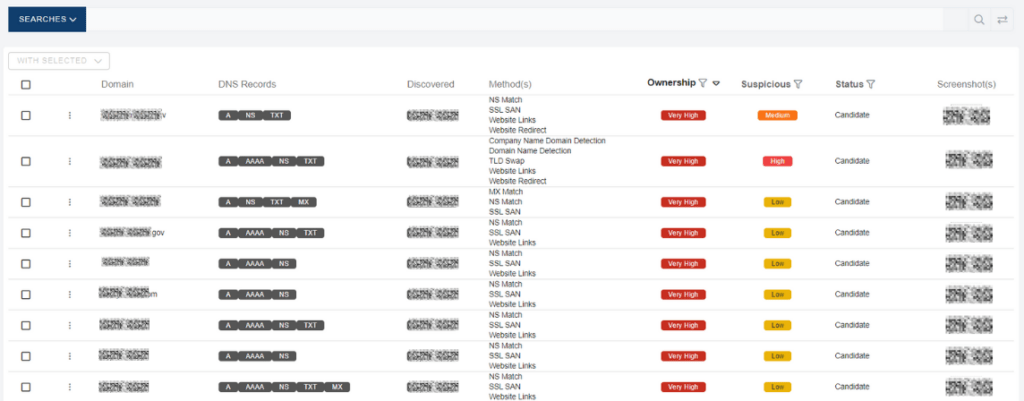
- Brand Protection Keywords
Brand-related keywords boost the Platform to discover even more domains, that either belong to your company or can pose a domain squatting threat. You want to benefit from this feature to protect your company’s brand from phishing and other harmful activity and to complete your scope definition.
Explore brand protection use-case for more insights.
Why should you care about mapping unknowns?
You can’t protect what you don’t know. The scope definition should be continuous as a company’s attack surface is dynamic. Constant mapping and scanning of all security issues allows you to stay up to date with online attack surface changes. External Attack Surface Management is a powerful, must-have situational awareness tool. It helps to find, assess, and report on all the assets and vulnerabilities associated with your organization. Situational awareness helps you to make sure that your security measures are up to date and your organization follows regulatory requirements. Knowing the whole attack surface lets you decide where to invest in stronger security. This guarantees the safety of your organization’s data and operations. Knowing the whole attack surface lets you decide where to invest in stronger security. This guarantees the safety of your organization’s data and operations. And thanks to EASM’s automated mapping and scanning features, you can easily take preventive measures to protect your organization from constantly changing threats.
Request your personalized demo
Curious to see what the Sweepatic External Attack Surface Management Platform can do for your organization? Request a personalized demo!
Follow us on LinkedIn and Twitter and subscribe to our newsletter to get the scoop on company news and new blogposts!
Watch this space to learn more about the ins and outs of EASM, its use cases, and tech talks.



